The Cyber Resilience Act (CRA): Mandating product security
Europe’s CRA integrates essential cybersecurity requirements into the familiar CE label, which is mandatory for products accessing the unified European market. Historically, the CE label ensured general safety like a baby toy not poisoning children or a battery not catching fire. The CRA expands this to include cybersecurity as a fundamental requirement for “products with digital elements,” encompassing nearly all software and hardware, including remote data processing solutions.
The CE label under the CRA will bring a minimum expectation of cybersecurity and include broad requirements that have been lacking globally. It mandates that manufacturers ensure products are secure by design, based on thorough risk analysis, and are released without known exploitable vulnerabilities. Products must also be patchable at no cost within a reasonable timeframe, and manufacturers are responsible for ongoing vulnerability management throughout the product’s lifecycle.
Manufacturers are accountable for design, implementation, verification, governance, and operations. Crucially, on the operational level the CRA introduces a concept of shared responsibility. Manufacturers must facilitate a product’s secure operation, providing specific guidelines to customers. Importers and distributors share in this collaborative accountability.
The CRA came into force on December 11, 2024. By September 11, 2026, manufacturers must notify market authorities if any product they have ever placed on the market is actively exploited. Full compliance is required by December 11, 2027. The CRA leverages harmonised standards by entities like CEN, CENELEC, and ETSI. Implementing these provides a “presumption of conformity,”, simplifying CE label acquisition.
OWASP SAMM: A framework for CRA compliance
SAMM is an acronym for Software Assurance Maturity Model. It is an open-source framework, designed by Open Web Application Security Project (OWASP) that provides a measurable approach to implementing and managing application security in organisations, both large and small. Given the stringent regulatory requirements and deadlines, OWASP SAMM can serve as a powerful tool to prepare organisations for product security certification and legislative compliance and guiding them in building a robust secure development lifecycle (SDLC).
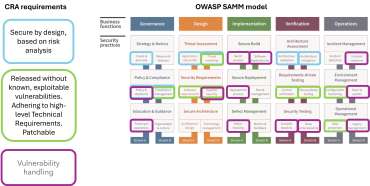
The model, as presented in the visual, is based on five business functions: governance, design, implementation, verification and operations. Each function consists of three security practices that each include two so-called streams. After completing a SAMM assessment, a score is presented per practice and stream, which gives the baseline for maturity of the application security practices in an organisation.
SAMM has now been specifically mapped to the EU CRA, categorising requirements into the mentioned three key areas that align with the CRA’s structure: “secure by design,” “released without risk of vulnerabilities,” and “vulnerability handling”. This mapping provides a practical and flexible framework for implementing the CRA’s demands. While there is an overlap in activities across these categories, different people and processes are often involved in each, making a structured approach essential.
The crucial role of the Security Champion
Transitioning to certifiable, secure by design and secure by default products is a challenging journey, often taking at least two years. Traditional roles like CISOs (focused on business/IT risks) or CTOs (sometimes lacking security context), as well as individual developers (finding strategic aspects too abstract), often fall short in owning this product security strategy. This underscores the need for a dedicated Security Champion.
Typically a technically proficient individual – an architect, lead developer, or technical expert – this Security Champion acts in an advisory role. Embedded within the development process and supported by the organisation, their role is to ensure teams have the necessary knowledge, tools, and structure to embed security into their daily work, recognising that product security is “everyone’s job”. Finding and empowering such a champion in an organisation can significantly accelerate this typical two-year journey.
Implementing SAMM assessments
For effective CRA preparation, SAMM assessments should not be high-level but concrete and scoped, focusing on a single product or a similar set of products, assessing individual teams or verticals that share a common SDLC. These assessments should consider the company’s history, markets, organisational structure, internal and external security drivers (like the CRA), past efforts, and historic incidents.
The Security Champion acts as an interpreter, bridging the gap between abstract security requirements, like those from the CRA, and developers’ day-to-day work, guiding them what needs to be done, how to do it and how to improve. While the champion translates results, the team owns the timeline and integrates SAMM into their workflow. The SAMM skills framework helps visualise shared responsibilities, mapping roles to security activities and stakeholders, clarifying ownership and suggesting training for individuals in the SDLC.
Measuring progress
While the team owns the roadmap, the CISO will still want a metric to measure success. SAMM can offer that, provided you set the right goals. And while scores and targets are important, they are relative. The focus should instead be on enabling teams to measure their own progress. This involves setting a baseline score, conducting regular reassessments to track progress, and defining a target score relative to the organisation’s context, risk appetite, team maturity, and legislative demands. A “percentage to target” is a good metric to quantify progress and helps prioritise activities. The underlying numbers matter less than the consistent movement forward.
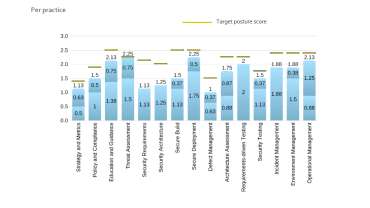
SAMM also assists Security Champions in identifying common gaps across teams to roll out centrally supported initiatives, like training programmes, to uplift overall security posture. Regular SAMM assessments are recommended every 12 to 24 months, with progress reported every 3 to 6 months. These should ideally be conducted through interviews for deeper understanding and coaching. SAMM scores are relative to each team’s context and scope, making direct comparisons between teams challenging.
Building a robust product security approach
The push for product security legislation is not confined to Europe, with regulations emerging in the UK (PSTI Act), India, Singapore, and Japan, among others. This trend underscores that robust processes for securing products and empowering organisations to implement them are essential, regardless of where you put a product on the market. Trying to “pour security sauce” over products after they are developed is unsustainable and does not scale.
To build a robust, CRA-compliant product security approach, organisations must find and empower Security Champions, divide work for CRA compliance by identifying gaps and assigning responsibility, set relative targets aligned with team contexts, support teams with resources, training, and tools, and consistently measure progress through regular assessments.
By embracing a structured approach like OWASP SAMM and fostering a culture of shared responsibility, organisations can ensure compliance and confidently deliver secure products in an increasingly demanding global market.








