A holistic approach to application security
An introduction to OWASP SAMM, an open-source application security maturity model
Why certification is not enough
When it comes to adopting a systematic approach to application security, there are a few options for companies to look at. The first one would be a certification-focused approach, based on compliance frameworks such as ISO27001 or SOC2. While these certainly have their merits, there are a few things to consider. The first is that compliance does not necessarily equal security. Too often companies strive for compliance to protect themselves against an auditor and not against an attacker.
Moreover, these certifications are not focused on application security but rather on security in the whole organization, and therefore often remain at too high a level. And finally, they do not provide a fine-grained measurability. You either have the certification or you don’t. In short, certification has a few shortcomings if companies decide to rely on them as the only framework to manage application security. So, the other option is to look at an application security programme such as SAMM.
OWASP SAMM: a measurable path to elevated application security
SAMM is an acronym for Software Assurance Maturity Model. It is an open-source framework that provides a measurable approach to implementing and managing application security in organizations, both large and small. It foresees an actionable plan to improve maturity levels and is versatile in the way that it covers technology, processes, and people. SAMM was designed by Open Web Application Security Project (OWASP) and takes a prescriptive approach, meaning it tells you what you should be doing, not what everybody else is doing.
There are numerous ways in which SAMM can be used by an organization. First, you can deploy it to evaluate your existing security processes. You can also use it to build a plan to improve in well-defined iterations in time and space or to define and measure security-related activities. And for sure, it allows organizations to demonstrate concrete improvements and progression based on scores from a security assurance programme. SAMM is even used by companies to assess the security depth and resilience before acquiring other companies.
A versatile and complete model
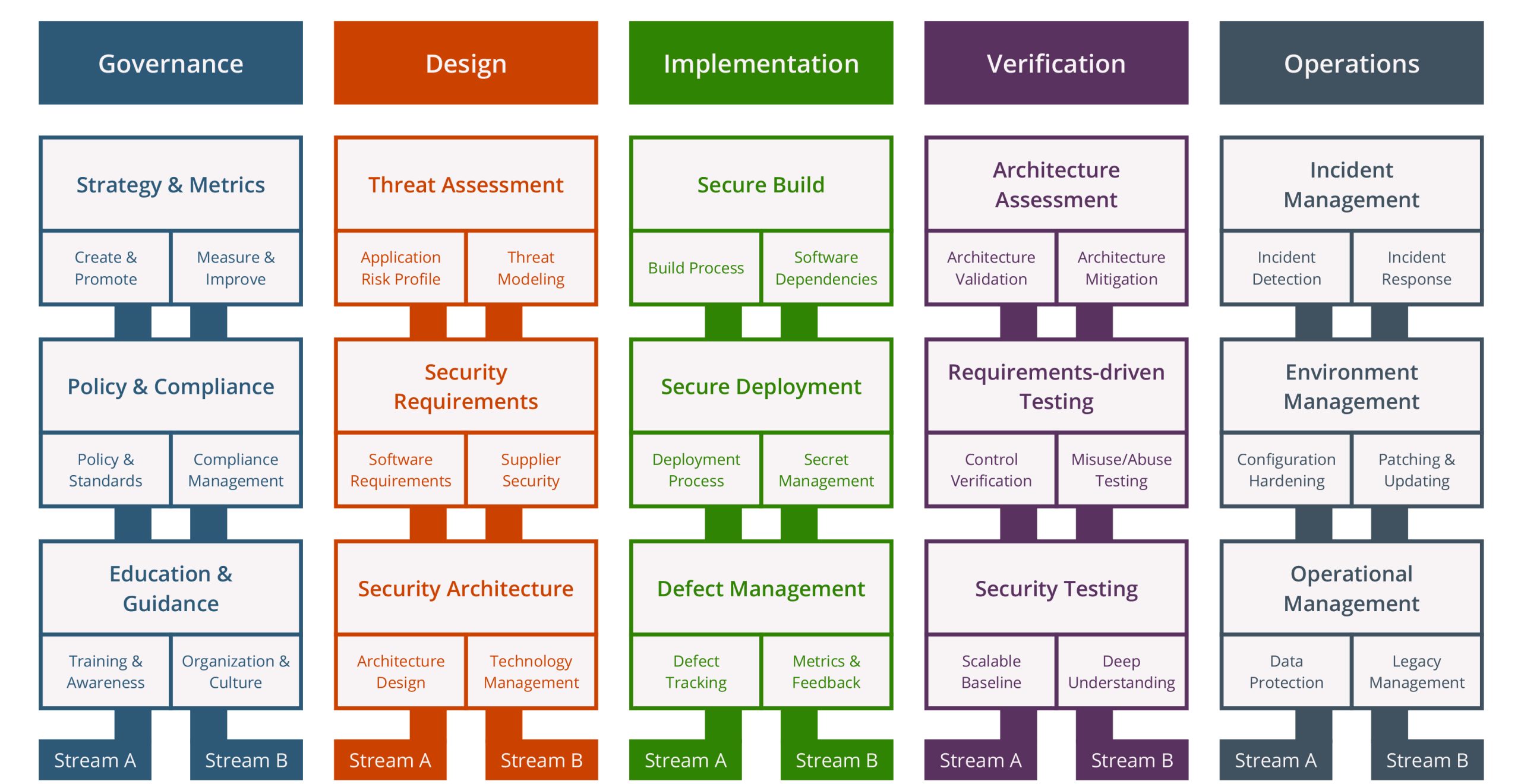
The model, as presented in the visual, seems a bit overwhelming at first, but it covers the whole framework. At the top there are five business functions that resonate well with all stakeholders. Governance and operations are typically situated at the level of the business/organization, while the other functions – design, implementation and verification are typically found at the level of the team.
Each function consists of three security practices that each include two streams. For each stream there are three maturity levels, with a score in between zero and three. For stream A ‘Training and awareness’ in the ‘Education and Guidance’ practice, for example, level one could involve providing training to people involved in the SDLC. Level two could include bringing more efficiency and effectiveness through automation, and the highest level of maturity would cover for instance measuring and improving processes and having feedback loops to other activities.
In total the answer to ninety questions (five practices x three security practices x two streams) will give you a score. Each question includes quality criteria to provide context and correct interpretation to the question’s topic. If you don’t meet one of the criteria, the answer to the question is by definition ‘no’. After completing the entire SAMM assessment, you get a score per practice and stream, which gives you the baseline for maturity of the application security practices in your company.
Implementing SAMM and stimulating its adoption
In large organizations, implementing SAMM is best governed by a company-wide task force in charge of application security. It collaborates with the teams, oversees processes and the acquisition and use of tools, shares knowledge, provides guidance and best practices. This task force also assists with governance and operations aspects, including strategy, policies, standards, compliance, training, incident management, configuration hardening and updates.
A great way to stimulate implementation and adoption of SAMM is gamification. Teams can compare their scores and compete with other teams to improve scores. Obviously, when organizing this, organizations should be aware that target scores are to be defined by risk tolerance. Concretely, getting a maximum score can be a waste of resources if this score is not really needed for a specific team or stream.
Navigating the challenges
OWASP SAMM’s strength as a generic model can be a double-edged sword for implementation. The open interpretation allows for adaptation across different teams, but this flexibility can lead to challenges in applying the framework consistently. Self-assessments might be subjective, and teams may potentially dismiss practices as inapplicable to their specific context.
Another question lies in addressing the above-mentioned risk-based scoring issue. An organization could, for instance, implement ‘corporate’ target scores, but that may direct teams towards taking the path of least resistance and overachieving on less important topics. One possible solution to tackle this is to introduce a ‘percentage to target score’ combined for instance with a bonus and/or penalty system.
The challenge remains, however, to define target postures for each team based on their risk profile, as each team is indeed unique. There is currently an OWASP SAMM benchmarking project ongoing that is collecting data for comparison all around the world to facilitate this definition process.
Finally, it has become clear that additional guidance is needed for so-called embedded teams that handle for instance printers, scanners or IoT devices. Also, further refinement of the model is necessary in terms of architecture assessment Practice and quality criteria consistency.
Driving application security maturity from awareness to action
OWASP SAMM offers a powerful approach to application security by offering a measurable way to track progress. This structured method allows organizations to objectively assess the effectiveness of their security programmes. Furthermore, SAMM can be gamified to boost employee awareness and engagement, contributing to the creation of a positive security culture. This gamification approach can even serve as a model for leveraging other security frameworks within the company.